Zero Trust
• 6 min to read •
Syxsense Zero Trust is a new module within Syxsense Enterprise that enables endpoint compliance with Zero Trust Network Access policies (ZTNA). This module is designed to serve as an organization's 'Trust Evaluation Engine' for endpoints.
The Zero Trust philosophy relies on a simple idea - 'Deny by Default' which means that if a user, device, or service asks for access to a company-owned resource (be that a web portal, a PowerPoint slide, or payroll information), the access to that resource is automatically denied by default. Relying on this idea offers unparalleled visibility and control over network access policies, and enables security teams to build sophisticated access policies and remediation workflows to ensure ZTNA compliance.
The specific features of Syxsense Zero Trust include:
- Complete visibility into all endpoint configuration and state of compliance using a single agent
- Build sophisticated access policies based on a large array of configuration and security parameters, setting unique policies for each individual corporate asset.
- Automate the immediate enforcement of access policy requirements and remediation of non-compliant endpoints using the Syxsense Cortex remediation engine.
- Verify trusted user authentication requests via the Syxsense console or optionally, connect with external multi-factor authentication(MFA)tools to provide a 'go, no-go' security status of devices. For example, if a customer uses Duo, Okta, or other MFA tools, simply connect those tools with the Syxsense API and it will report compliance on each endpoint looking to access corporate assets.
Within Syxsense, there are two primary components to Endpoint Oriented Zero Trust, Security Postures and Resources. Security Postures are cortex policies that run locally on an endpoint, evaluating the state of a device. Resources are the websites, applications, and services that are to be allowed or blocked based on the results of a Security Posture. When a security posture and set of resources are united, we form a Trust Evaluation, the basic formed relationship formed within Endpoint Oriented Zero Trust.
| ❶ |
Click the Zero Trust tab within the Syxsense console sidebar ① Select the Trust Evaluations tab ② Click the Create button ③ The toolbar in the top section also provides multiple other options for managing existing Trust Evaluations, like editing, deleting, publishing, exporting, and configuring evaluation settings ④ Create a name for your new trust evaluation ⑤ Click 'Save' ⑥Drop-down TitleDrop-down Title 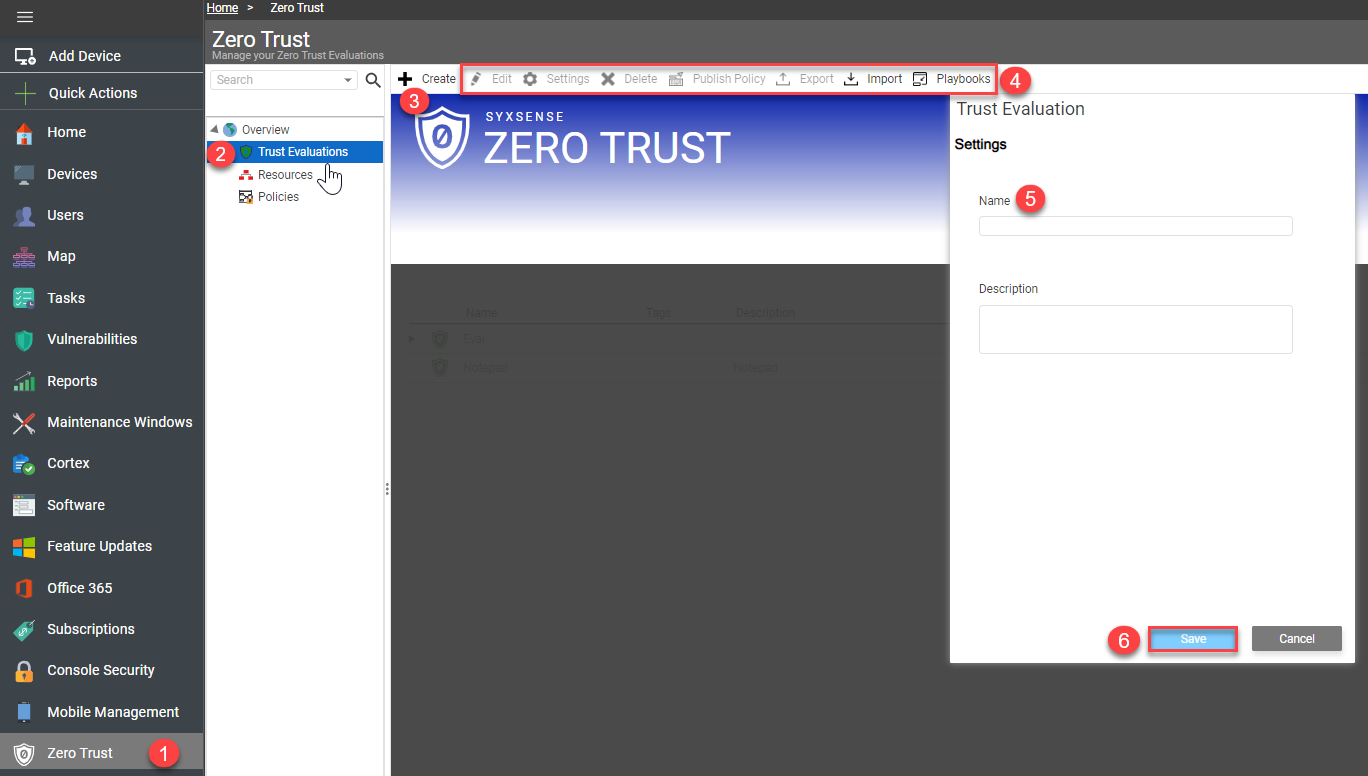 |
| ❷ |
Next you will be moved into the Security Posture workflow canvas. This canvas is familiar to Syxsense Cortex canvas. If you have not yet used the Syxsense Cortex automation engine, please review the Syxsense Cortex chapter before continuing further. The only major differences between the Security Posture canvas and the standard Cortex canvas are the new panel on the left-hand sidebar ①, and a changed set of actions on the right-hand sidebar ② To build a Security Posture (e.g. create a zero trust evaluation that checks if an anti-virus agent is installed), select the 'Find Software' action from the Actions sidebar ③ and drag the action onto the main canvas ④ This 'Find Software' action will act as the triggering function for our Security Posture.Drop-down TitleDrop-down Title 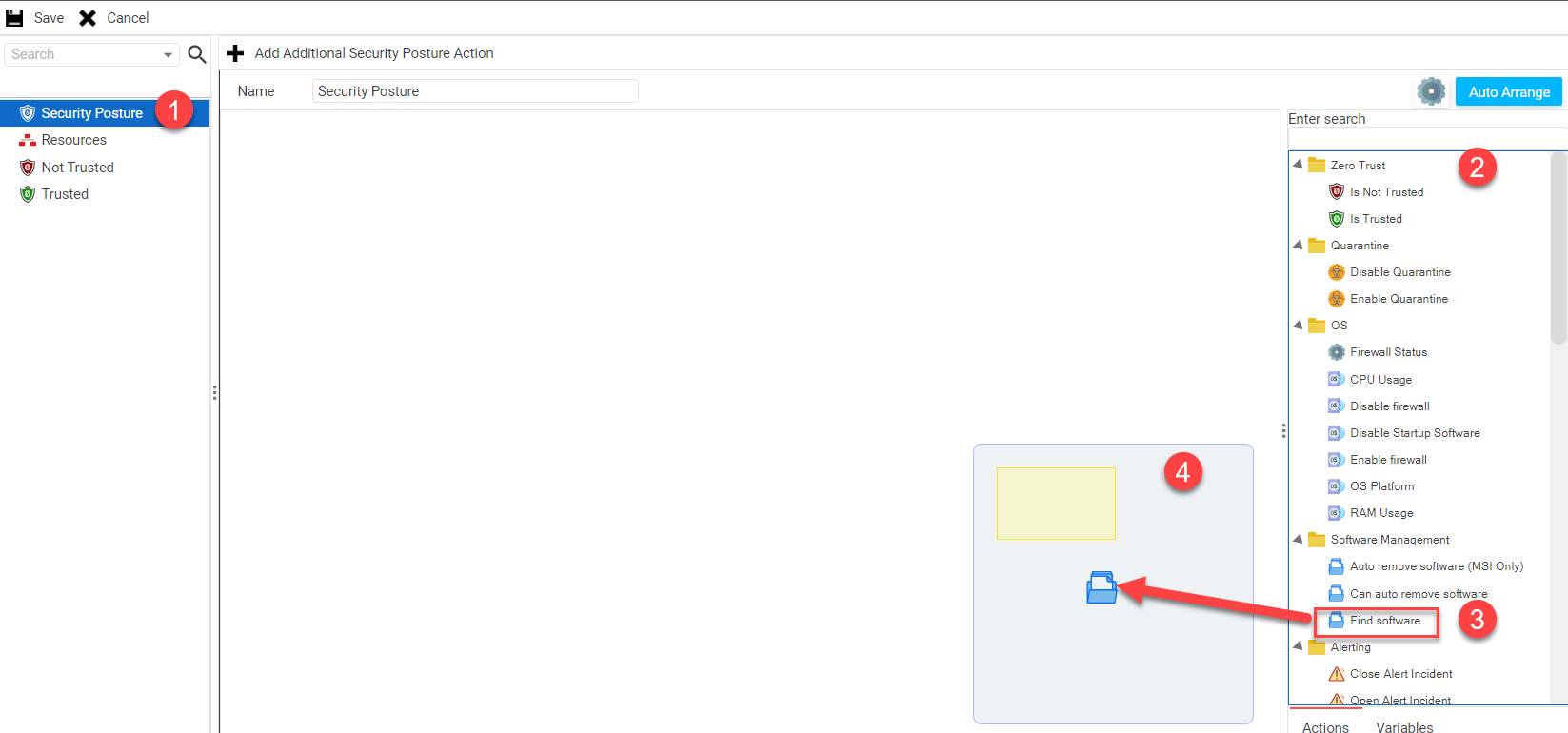 |
| ❸ |
Then, from the find software action window, type in the name of your Anti-virus product ⑤ Optionally, select the Partial match option if you are not confident in the exact naming convention for your AV product ⑥ Save ⑦Drop-down TitleDrop-down Title 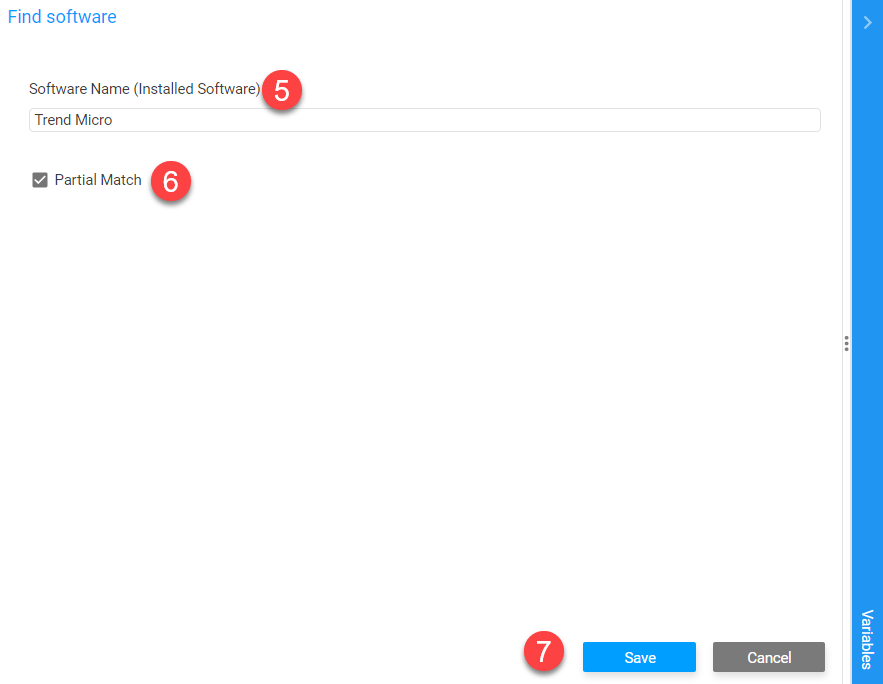 |
| ❹ |
To establish a trust relationship to the Find Software action, select 'Is Not Trusted' from the actions sidebar ⑧ Drag it over to the Not Found state node for the 'Find Software' action in the canvas ⑨ This will establish that if the required anti-virus agent is not found on a device, then the endpoint is not trusted.Drop-down TitleDrop-down Title 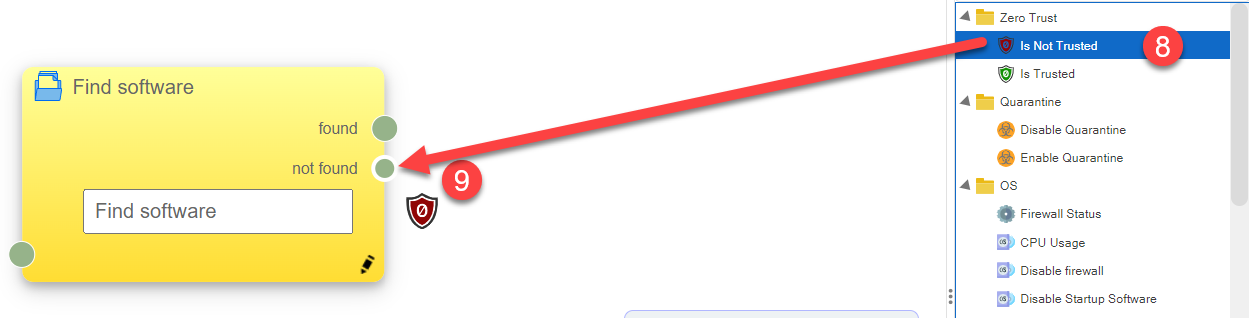 |
| ❺ | Connect the 'is Trusted' action ⑩ to the Found state on the 'find software' action ⑪Drop-down TitleDrop-down Title
 |
| ❻ | Once both the trust states are defined, your new trust evaluation should look like the following canvas Drop-down Title Drop-down TitleDrop-down Title
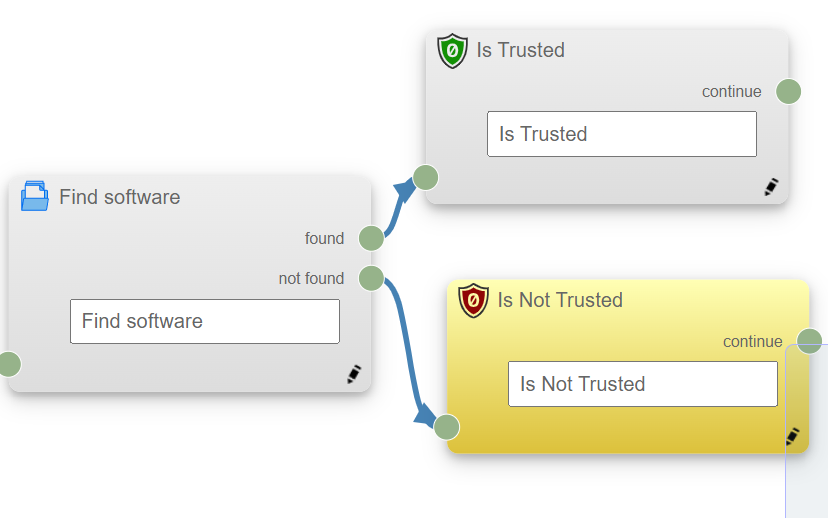 |
| ❼ |
Create a set of resources to apply to the trust evaluation. To create a new resource, select the Resources tab from the trust evaluation canvas sidebar ① Select the Create button to build a new resource ② As with the Trust Evaluation creation, when you select the create button for a new resource, it will prompt you to provide a name for the resource ③ Click 'Save' ④Drop-down TitleDrop-down Title 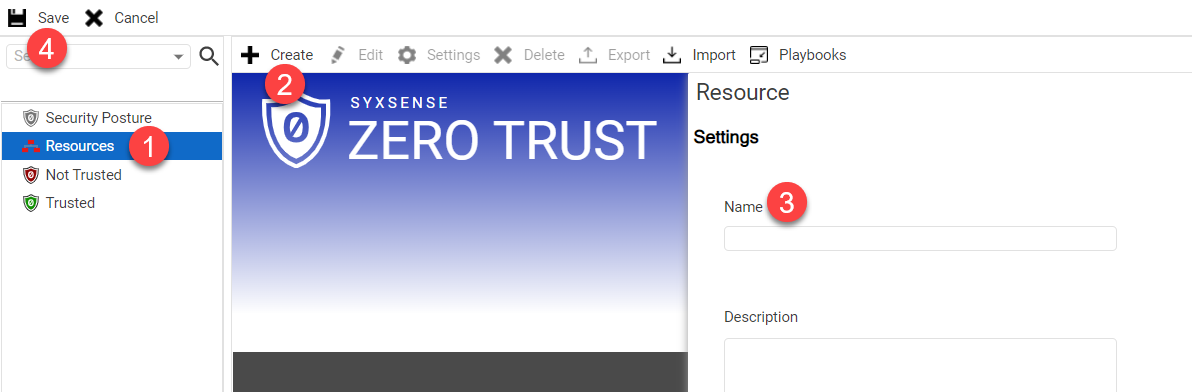 |
| ❽ |
After naming your resource, you will be taken to a new cortex-style Resource Workflow canvas. For this example, we are going to create a trust resource for the Microsoft Teams instant messaging application. When we entered the Resource Workflow canvas, we automatically enter the Not Trusted resource context ① If you want to build a Trusted resource, simply select the Trusted tab from the sidebar ② To build a Not Trusted resource to close teams, within the actions sidebar, select the Kill Process action ③ then Drag it onto the canvas ④Drop-down TitleDrop-down Title 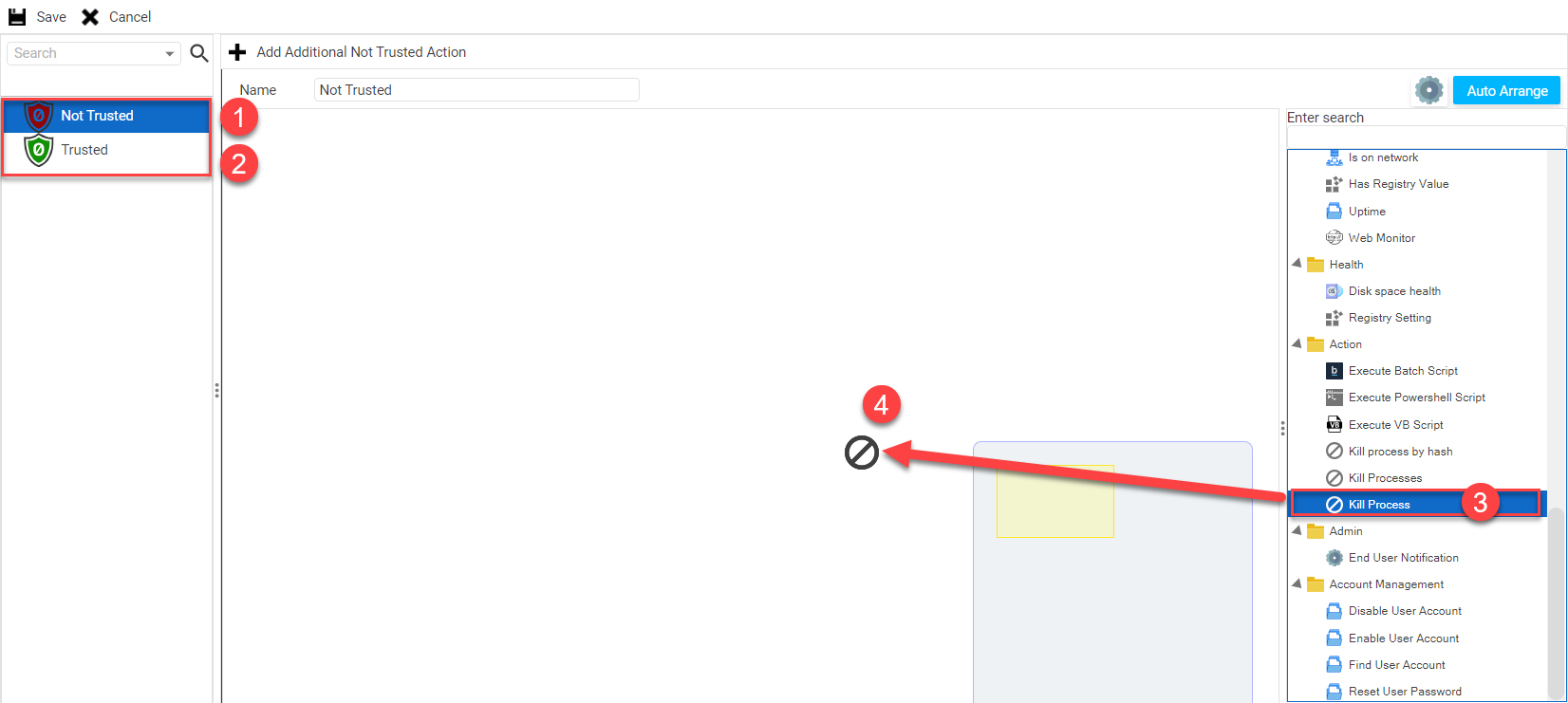 |
| ❾ |
Once placed onto the canvas, the Kill Process action will prompt you for a process to end ⑤ For this example, we are ending the 'teams.exe' process. Once that value has been input, select the save button ⑥ In this example, the only component to our trust evaluation resources is a task that kills the teams.exe service if it is found to be running when the device is in an untrusted state. When the device returns to a trusted state, the Kill Teams action will no longer be running, and teams will open successfully without intervention. To finalize this Resource, select the Save button in the upper left. If you want to add additional Not Trusted actions, you can do this by selecting the button in the toolbar.Drop-down TitleDrop-down Title 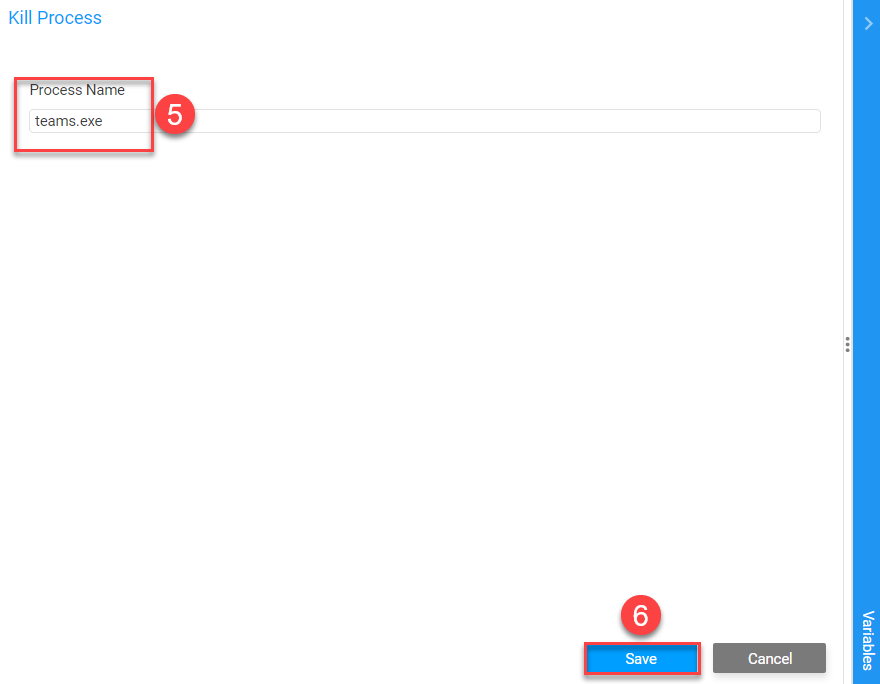 |
| ❿ |
Enable the Resource from within the Trust Evaluation main panel: Select the Resources tab ①, and then select the name of the resource you just built ② Save the evaluation by selecting the save button in the upper left corner of the Trust Evaluation window.Drop-down TitleDrop-down Title 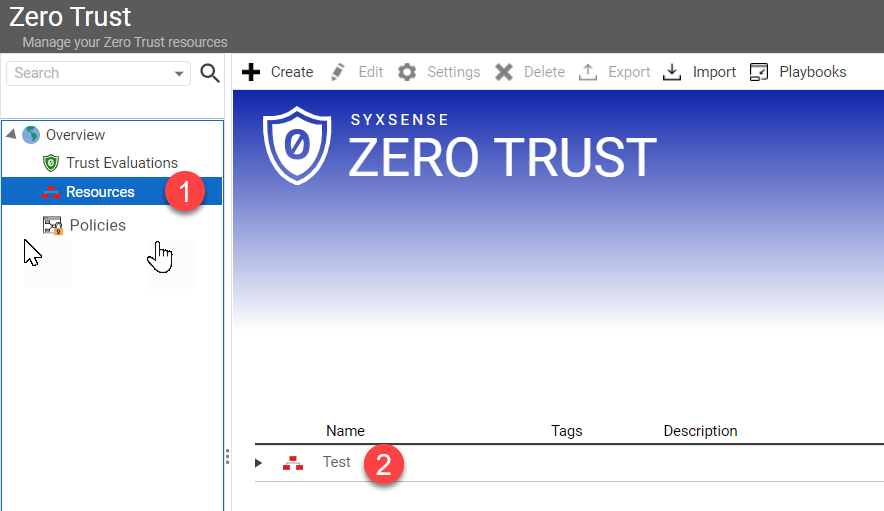 |
| ❶ |
To deploy a trust evaluation, from the Zero Trust Console, select the Trust Evaluations sidebar tab ① Then, select the name of the trust evaluation you want to deploy ② Next, select the Publish Policy button from the top toolbar ③Drop-down TitleDrop-down Title 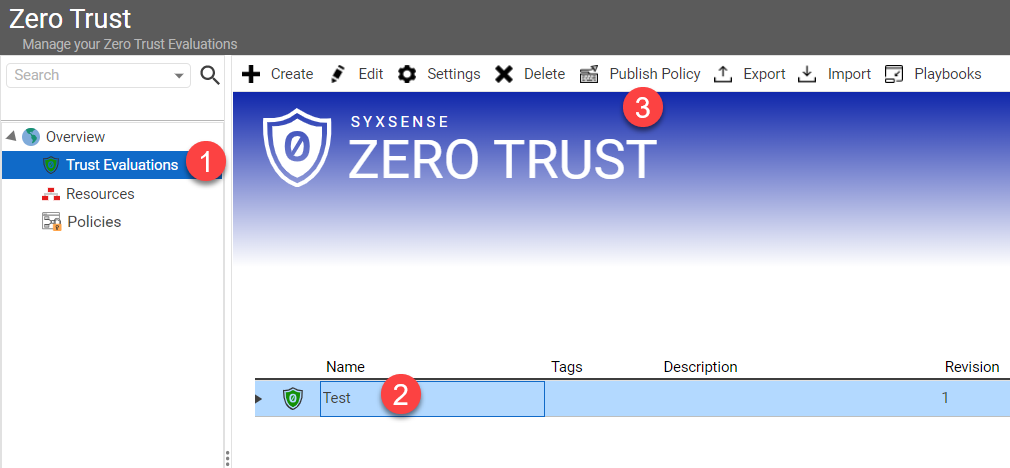 |
| ❷ |
Once you have opened the Publish Policy option, you will be prompted to configure the Trigger interval, schedule, blackout hours, and target devices for your Zero Trust Policy. The default option for triggering a Zero Trust policy is to evaluate the security postures of the Trust Evaluation every 10 seconds. This frequency can be reduced or increased as needed. But a 10-second interval generally provides the fastest yet most stable option available within the product. |
| ❶ |
To review active Syxsense Trust Evaluations, please go to the Zero Trust console page, and then select the Policies tab ① From the Policies tab, you can review all of the currently created Trust Evaluation policies. To cycle the state (on or off) of a Trust Evaluation policy, simply select the toggle to the left of the policy name ②Drop-down TitleDrop-down Title 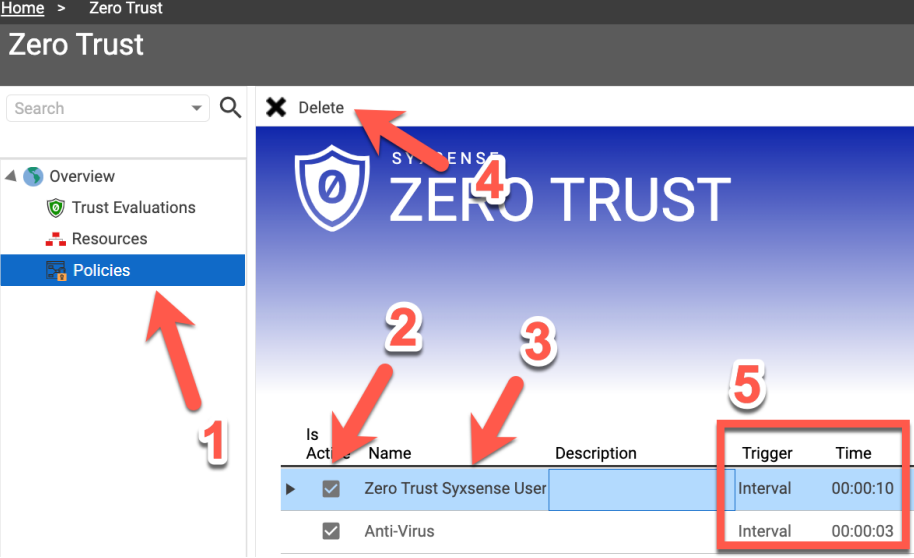 |
| ❷ | To delete an existing policy, select the row for the policy ③, and then select the 'Delete' button from the top toolbar ④ |
| ❸ | From within the Policies tab, you can also visualize the triggering mechanisms in use by existing Zero Trust policies, as well as the frequency of evaluation ⑤ |
Video Tutorials: Examples of Trust EvaluationsVideo Tutorials: Examples of Trust Evaluations
Watch an example of creating a Trust Evaluation: Check the clock Video
Watch an example of creating a Trust Evaluation: Check the status of Firewall Video
Watch an example of creating a Trust Evaluation: Only trust machines on Site Video
Watch an example of creating a Trust Evaluation: Trust if Realtime AV is on Video
Watch an example of creating a Trust Evaluation: Trust machines only during working hours Video
Last Update: July, 2024
Copyright ©2024 by Syxsense, Inc. All Rights Reserved