Security Content Library
In addition to curating patch content, Absolute also provides configuration content within the Vulnerabilities library. The main differences between patch content and configuration content are the discovery process and the payload delivery method.
When evaluating devices for configuration vulnerabilities, a script that scans filesystems, registries and software configurations for flags, text entries, or file versions (among many other types of searches) is deployed. If a script triggers on something, that item triggers the denotation of a found configuration vulnerability on the endpoint.
The Security Summary provides similar information to the Patch Summary, but instead focuses on summarizing the vulnerability, script components, and security configurations. If the vulnerability is repairable, you can also review the Resolution Workflow (under Patch Status on the left ) to apply fixes and track remediation progress.
Queries and Groups
System security is crucial to protect your system from cyber-attacks. It is provided in 2 steps:
① Security Scan which allows detecting malicious processes and misconfigurations on the devices in the corporate network.
② Security Resolve which allows automatically fixing most of the detected security flaws via tested resolution workflows.
Discovery: Security Script OverviewDiscovery: Security Script Overview
To review the scipts library, start by navigating to the Vulnerabilities tab in the Console menu.
Select the Security tab within the Vulnerabilities sidebar.
Once the Scripts Library view has populated, you will see a long list of security scripts arrayed in a table, as shown below.
The following information can be used for filtering the table columns .
| Repairable |
The indicator of the issue reparability. To see which security items can be resolved in the Absolute console, sort them by Repairable column within the column set for the security definitions: No - A vulnerability can't be automatically resolved, Cortex remediation is not available. Yes - A vulnerability can be automatically resolved, Cortex remediation is available. |
| Approved |
This indicates if a repairable script is ready for deployment. Used for approving multiple security remediation workflows for deployment without additional review of each workflow.
It is recommended to thoroughly research the remediation workflow before approving it for deployment, as the applied changes may pose a danger to your system configurations. |
| State | The indicator of the device that has a particular flow. |
| Title | The name of the vulnerability. |
| Description | The information about the vulnerability. |
| CVSS | The independent CVSS score represented as the number (You can also switch on and off a color indicator by checking/unchecking the checkbox with an empty row below). |
| CVSS Severity | The independent CVSS score represented as a title (You can also switch on and off a color indicator by checking/unchecking the checkbox with an empty row below). |
| Severity |
Absolute-issued severity level:
|
| Vendor | Absolute |
| Language | INTL |
| CVEs | Lists the Common Vulnerabilities and Exposures identifiers associated with the vulnerability. |
| Date Published | The date the script was published. |
| Is Reboot Required | Specifies whether a system reboot is necessary after applying the script. |
| Public Aware |
The method to expose the vulnerability is publicly aware. Publicly Aware vulnerabilities are often weaponized and therefore should be prioritized before they become weaponized. |
| Counter Measure | An alternative solution exists where the patch can be mitigated, see vendor for full details. |
| Weaponized |
The vulnerability is currently being exploited. Weaponized vulnerabilities should be treated as Zero-Day ones and deployed urgently. |
You can also refine security script content by device using the Device Targeting Wizard.
This feature allows you to specify a list of assets, narrowing down the scope of security scripts to only those relevant to the specified endpoints.
Further filtering can be obtained by searching for specific content using the Search Input box.
Currently, Absolute supports the following searches:
| Title | Vulnerability name (crafted by Absolute) |
| Description | Vulnerability description provided by Absolute |
| CVE | The Vulnerability Identity provided by Mitre Corporation |
| HelpFileID/Syx-ID |
The Vulnerability Identity provided by Absolute. This unique HelpFileID is correspondent to the last characters in vulnerability URL before .html in Vulnerabilities Database |
Discovery: Security FamiliesDiscovery: Security Families
In addition to the standard attributes available to Absolute patch content, the Absolute security content library also has an attribute for the family of vulnerabilities to which the security definition belongs.
Each of the vulnerabilities belongs to a different classification called a Family. Using these Families, you can scan for specific types of vulnerabilities without the need to scan for everything e.g., scanning just for BitTorrent programs.
All information about known vulnerabilities and the description of each family are available in our Vulnerabilities Database.
| AD FS Hardening | A security family consisting of definitions to detect which actions are required to harden Active Directory Federation Services (AD FS) |
| Antivirus | A security family consisting of definitions to detect common Antivirus product definition status and frequency of scans. |
| Backdoors | A security family consisting of definitions to detect common backdoor applications. |
| Browser Extensions | A security family consisting of definitions to detect common vulnerabilities in browsers extensions. |
| Browsers | A security family consisting of definitions to detect common browsers vulnerabilities. |
| CIS Benchmarks | A security family consisting of definitions to detect which actions are required to maintain compliance with the CIS Benchmarks. |
| Crypto Mining | A security family consisting of definitions to detect traces of cryptocurrency mining. |
| Databases | A security family consisting of definitions to detect common Database vulnerabilities. |
| Drivers and Hardware | A security family consisting of definitions to detect common hardware and drivers' vulnerabilities. |
| Engineering and Development Software | A security family consisting of definitions to detect common engineering and development software vulnerabilities. |
| Firewalls | A security family consisting of definitions to detect common vulnerabilities in firewall software. |
| FTP Software | A security family consisting of definitions to detect common FTP software vulnerabilities. |
| Graphics Software | A security family consisting of definitions to detect common graphics software vulnerabilities. |
| Legacy and Out-of-Support Software | A security family consisting of definitions to detect software that is no longer supported. |
| Microsoft 365 Apps | A security family consisting of definitions to detect common security threats in Microsoft 365 Apps. |
| Miscellaneous | A security family consisting of definitions to detect vulnerabilities that do not fit any of the represented categories. |
| .Net Core Vulnerabilities | A security family consisting of definitions to detect common vulnerabilities detected in .NET Core. |
| Peer-to-Peer File Sharing (Applications) | A security family consisting of definitions to detect common P2P sharing applications. |
| Peer-to-Peer File Sharing (Binary) | A security family consisting of definitions to detect common P2P binaries. |
| Policy Compliance | A security family consisting of definitions to detect common compliance items like anti-virus usage, firewall status, and full-disk encryption status. |
| Port Scanner | A security family consisting of definitions to detect vulnerable ports. |
| Post Patching | A security family consisting of definitions to detect which post patching activity is required. |
| Privacy | A security family consisting of definitions to detect common vulnerabilities which affect users' privacy. |
| Remote Desktop | A security family consisting of definitions related to remote desktop connections. |
| RPC | A security family consisting of definitions related to remote procedural calls. |
| SNMP | A security family consisting of definitions related to network management traffic. |
| Social Networking | A security family consisting of definitions to detect vulnerabilities in social networking software. |
| VPN Software | A security family consisting of definitions related to the VPN software. |
| Virtualization | A security family consisting of definitions related to virtualization software. |
| Web Servers | A security family consisting of definitions to detect common vulnerabilities and security issues in web servers. |
| Windows Configuration | A security family consisting of definitions to detect common overall Windows configuration vulnerabilities. |
| Windows Policies | A security family consisting of definitions to detect faulty Windows security policies. |
| Windows User Accounts | A security family consisting of definitions related to Windows user security, account statuses, and local settings. |
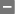 The script is not repairable
The script is not repairable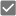 Approved for deploy
Approved for deploy Not approved for deploy
Not approved for deploy